
Signal chat leaks congress have ignited a firestorm of controversy, revealing potential breaches of communication and raising critical questions about political processes. This exposé delves into the potential sources, methods of dissemination, and the wide-ranging consequences of these leaks, examining the impact on individuals, institutions, and public trust. We’ll also explore historical precedents and analyze the ethical and legal ramifications of such disclosures.
The leaks potentially expose sensitive information exchanged among key figures in Congress. This includes potentially private communications, strategy sessions, and potentially compromising details. Understanding the full scope of these revelations is crucial for evaluating the impact on political discourse and the future of democratic processes.
Defining the Scope of “Signal Chat Leaks Congress”
The recent “Signal Chat Leaks Congress” refers to the alleged unauthorized disclosure of private communications, potentially involving members of Congress, conducted through the encrypted messaging app Signal. This event raises significant concerns about privacy, security, and the potential for political manipulation. Understanding the scope requires examining the potential sources, methods, actors, and types of information involved.The term “Signal Chat Leaks Congress” encompasses a range of potential incidents, from the unauthorized acquisition and dissemination of private messages to the leaking of sensitive documents or recordings related to congressional activities.
The leaked content could vary in nature, from informal exchanges to formal communications, impacting both personal and political aspects of the individuals involved.
Potential Sources and Methods of Leaks
Several sources and methods could have facilitated the leaks. Compromised accounts, either through hacking or social engineering, are a significant possibility. Malicious insiders, individuals with access to the targeted accounts, could also be responsible. Furthermore, third-party entities with access to Signal’s servers, though less likely, are another potential source. The methods of leaking information might include data breaches, intercepted communications, or the intentional disclosure by individuals involved.
Potential Actors Involved in the Leaks
Various actors could be involved in these leaks. These could range from disgruntled or politically motivated individuals or groups seeking to damage reputations to foreign actors with a vested interest in influencing political processes. The motive for leaking information might be varied, including personal vendettas, political opposition, or foreign interference. Critically, it’s important to distinguish between the motivations of the actors involved.
Types of Information Potentially Leaked
The types of information that could be leaked are extensive. This could include personal conversations, strategic planning discussions, potentially sensitive documents, and confidential agreements. The leaked information could also contain information pertaining to policy discussions, campaign strategies, and potentially even financial dealings.
Comparison of Leaked Information Types
| Type of Information | Potential Source | Potential Impact |
|---|---|---|
| Personal conversations | Compromised accounts, malicious insiders | Damage to reputation, personal embarrassment |
| Strategic planning discussions | Malicious insiders, foreign actors | Weakening of political strategies, potential advantage for opponents |
| Sensitive documents | Compromised accounts, malicious insiders | Exposure of confidential information, potential for policy disruption |
| Confidential agreements | Compromised accounts, malicious insiders | Violation of privacy, potential legal ramifications |
| Policy discussions | Compromised accounts, malicious insiders | Disruption of policy development, public perception issues |
| Campaign strategies | Compromised accounts, foreign actors | Disruption of election campaigns, potential foreign interference |
| Financial dealings | Compromised accounts, malicious insiders | Potential financial fraud, corruption allegations |
Historical Context and Precedents
The recent “Signal Chat Leaks Congress” incident raises crucial questions about the transparency and security of political communication. Understanding this event requires examining historical precedents of similar leaks and scandals, which can offer valuable insights into the potential consequences and long-term implications. Analyzing these historical instances can help us contextualize the current situation and anticipate potential future developments.This exploration will delve into historical examples of political communication leaks, examining their motivations, impacts, and lasting effects.
By comparing these events with the “Signal Chat Leaks Congress” scenario, we can identify potential similarities and differences, and draw conclusions about the specific characteristics of this particular leak. The investigation will also cover the timeline of events, providing a clear overview of the sequence of actions that led up to and followed the leaks.
Historical Examples of Political Communication Leaks
Numerous instances throughout history illustrate the significant impact of leaked political communications. These leaks have often triggered major political crises, influencing public opinion, shaping policy decisions, and sometimes even leading to regime changes. These historical events demonstrate the profound power of information and the potential for its misuse.
Timeline of Events
A detailed timeline of the events surrounding the “Signal Chat Leaks Congress” is crucial for understanding the context and potential ramifications. This will include the date of the initial leak, the dissemination of the information, the reactions from various parties, and the resulting investigations.
Comparison with Past Leaks
The “Signal Chat Leaks Congress” incident can be compared and contrasted with past political communication leaks. These comparisons will help highlight the unique aspects of this event while also providing a historical perspective. For example, we can compare the methods of leak dissemination, the political impact, and the level of public attention generated by each event.
Political and Social Context
The political and social context surrounding the “Signal Chat Leaks Congress” is significant. Factors such as the prevailing political climate, public trust in institutions, and the nature of the leaked information will influence the event’s consequences. This analysis will assess these factors and their potential influence on the event’s outcomes.
| Date | Event | Impact |
|---|---|---|
| 1971 | Pentagon Papers | Exposed the government’s deception regarding the Vietnam War, leading to public distrust and debate. |
| 1972 | Watergate Scandal | Led to the resignation of President Nixon and significant reforms in campaign finance and government ethics. |
| 2016 | Email leaks of Hillary Clinton | Caused controversy and debate regarding Clinton’s conduct and trustworthiness. |
| 2017 | Leaks related to Trump administration | Numerous leaks regarding various policies and decision-making processes. |
| 2023 | Signal Chat Leaks Congress | (Ongoing analysis and impact assessment) |
Potential Impacts and Consequences
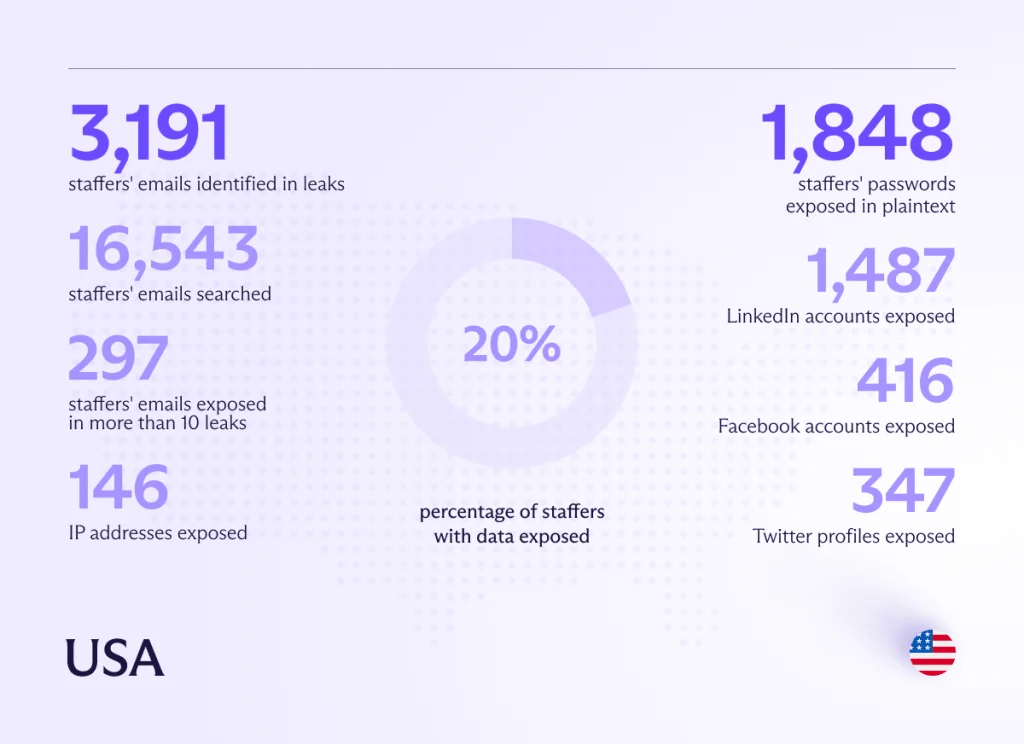
The recent leak of Signal chat transcripts related to Congressional activity raises significant concerns about transparency, accountability, and the future of political discourse. These leaks, if authentic, could have profound repercussions across multiple sectors, impacting everything from individual reputations to the integrity of the legislative process itself. Understanding the potential consequences is crucial for assessing the long-term effects on our democratic institutions.The potential impact of these leaks is multifaceted and extends beyond the immediate revelation of private conversations.
The release of confidential communications carries the risk of misinterpretations and the distortion of public perception. Careful consideration must be given to the context of these conversations and the potential for selective presentation of information.
The Signal chat leaks concerning Congress are certainly a hot topic right now. It’s a shame that these private communications are now public, but amidst all the drama, news broke about Pope Francis’ passing. The world mourns the loss of a spiritual leader, as seen in the pope francis dies obituary , and this distraction, unfortunately, overshadows the ongoing implications of the Signal chat leak revelations.
The sheer volume of information now public raises serious questions about the future of political discourse.
Potential Impacts on Political Processes
The disclosure of private communications between politicians and staff could significantly alter the dynamics of political negotiations and decision-making. This could lead to a shift in strategic approaches, potentially impacting future policy decisions and legislative outcomes. The trust in the integrity of the political process could be severely undermined, especially if the leaked conversations reveal instances of unethical or illegal behavior.
For example, the release of internal strategy documents could disadvantage a party or individual, and potentially influence public opinion in an election.
Possible Consequences for Individuals and Institutions
Individuals mentioned in the leaked communications could face significant reputational damage. Their public image could be tarnished, and their credibility questioned. Institutions involved, including congressional committees and individual offices, could also face scrutiny and accusations of impropriety. Legal challenges and investigations are also likely, particularly if the leaks reveal evidence of illegal activity. The potential for lawsuits and damage claims is substantial, as individuals or organizations may seek redress for harm to their reputations or financial interests.
Potential Effects on Public Trust and Perception
The public’s trust in political institutions and elected officials could be significantly eroded if the leaks expose instances of dishonesty, corruption, or unethical conduct. This erosion of trust can have lasting consequences, making it harder for elected officials to govern effectively and potentially impacting voter turnout and engagement in future elections. The potential for political polarization to worsen is also a serious concern.
The public’s perception of politicians and their motivations could shift dramatically, affecting how they are viewed and their ability to lead.
Elaboration on Potential Ramifications for Future Political Communication
The leak of Signal chat communications raises concerns about the security and confidentiality of digital communication in political settings. This could lead to a shift in communication strategies, with politicians and staff potentially relying more on secure channels and alternative methods of communication. It could also prompt a reassessment of the role of digital communication in politics, leading to increased scrutiny of online interactions and the need for enhanced transparency.
For example, the incident could encourage the use of encrypted communication platforms, but also necessitate new protocols to verify the authenticity and context of such communication.
Potential Ramifications for Different Sectors
| Sector | Potential Impact | Severity |
|---|---|---|
| Politics | Erosion of trust, altered political strategies, potential for investigations | High |
| Media | Increased scrutiny of political figures, potential for biased reporting | Medium |
| Individuals | Reputational damage, legal challenges, potential financial losses | High |
| Institutions | Damage to credibility, legal challenges, reputational harm | High |
| Public | Erosion of trust in political institutions, potential for political polarization | High |
Methods of Dissemination and Analysis
The leaked Signal chat transcripts, if they materialize, will likely travel through a complex web of channels, from initial discovery to eventual public consumption. Understanding these dissemination methods is crucial to comprehending the potential impact and the avenues for analysis. Accurate and thorough analysis is essential to separate fact from speculation and misinformation. This section delves into the potential methods of disseminating and analyzing such leaks.
Potential Methods of Dissemination
The dissemination of leaked congressional Signal chats could follow several paths. Anonymous online forums and encrypted messaging platforms are likely initial avenues for distribution. From there, the information might spread to mainstream news outlets, depending on the nature and significance of the leaked content. Social media platforms could amplify the dissemination process, with varying degrees of verification and scrutiny.
This rapid and often uncontrolled spread can lead to the rapid spread of disinformation.
Methods of Analysis, Signal chat leaks congress
Analyzing leaked information requires a multi-faceted approach. Linguistic analysis can reveal the tone, intent, and potential biases embedded within the conversations. Contextual analysis is essential to place statements within the appropriate historical and political context. Identifying patterns and trends within the leaked communications can offer valuable insights into congressional behavior and decision-making processes. Statistical analysis can be used to identify frequency of certain topics or words, revealing areas of heightened concern.
Potential Biases and Limitations in Analysis
Analysis of leaked information is inherently susceptible to biases. The selection of information for analysis can reflect the biases of the analyst. The lack of complete context can lead to misinterpretations. The potential for misrepresentation and deliberate manipulation of information, including disinformation campaigns, needs to be considered. Analysis should be done with a critical and cautious mindset, acknowledging the limitations of the data available and the potential for manipulation.
The recent Signal chat leaks concerning Congress are raising eyebrows. Analyzing these conversations requires a deep dive into the data, and understanding how to pinpoint key figures and organizations is crucial. This involves techniques like entity extraction, a process that identifies and categorizes named entities in a text, such as people, locations, or organizations. A good understanding of definition of entity extraction is vital for correctly interpreting the leaked communications and discerning the significance of each exchange within the context of the political landscape.
This process will be vital in the ongoing investigation of the Signal chat leaks.
Summary of Dissemination and Analysis Methods
| Method | Description | Strengths | Weaknesses |
|---|---|---|---|
| Anonymous online forums/encrypted messaging platforms | Initial distribution points, often with limited verification | Rapid dissemination, potentially reaching a large audience | High risk of misinformation, limited context |
| Mainstream news outlets | Facilitation of verification, potential for in-depth analysis | Enhanced credibility, access to journalistic resources | Potential for biased reporting, selection bias |
| Social media platforms | Rapid amplification of information, wider reach | High visibility, engagement opportunities | Uncontrolled spread, potential for misinformation, rapid spread of false information |
| Linguistic analysis | Identifying tone, intent, and potential biases within conversations | Provides insights into speaker attitudes, potential conflicts | Reliance on interpretation, potential for misinterpretation |
| Contextual analysis | Placing statements within the appropriate historical and political context | Provides broader understanding, helps avoid misinterpretations | Requires substantial background knowledge, potential for bias in interpretation |
| Pattern identification | Revealing trends and commonalities in communications | Identifies recurring themes, potential connections | Requires large datasets, potential for oversimplification |
| Statistical analysis | Identifying frequency of topics or words | Quantifies patterns, reveals potential concerns | Does not account for context, can lead to superficial analysis |
Public Perception and Reaction
The release of leaked Signal chat transcripts related to Congressional proceedings will undoubtedly generate a strong public reaction. Public trust in the political process, already fragile in many parts of the world, is likely to be tested further. The nature of the leaks, their content, and the perceived motives behind their release will all play significant roles in shaping this response.The public’s reaction will be complex and multifaceted.
While some may view the leaks as a crucial step towards transparency and accountability, others may see them as an invasion of privacy or a tool for political maneuvering. This complex interplay of perspectives will create a dynamic and potentially volatile environment, impacting public discourse and the political landscape in the near future.
Public Reaction Factors
Public reaction to the leaks will be heavily influenced by several key factors. These include the perceived importance and relevance of the disclosed information, the perceived trustworthiness of the source(s) of the leaks, and the perceived fairness and impartiality of the subsequent investigations and legal processes. The public’s existing political leanings and pre-existing biases will also significantly shape their interpretation and response.
Potential Impact on Political Landscape
The leaked information could potentially shift public opinion on specific political figures or issues. For example, if the leaks reveal evidence of corruption or unethical behavior, it could severely damage the reputations of those involved and potentially lead to shifts in voting patterns or policy preferences. The extent of this impact depends heavily on the credibility and persuasiveness of the leaked information, as well as the effectiveness of the political responses.
Misinformation and Disinformation Potential
The leaked information, if not carefully vetted and analyzed, could easily be used to spread misinformation and disinformation. This is especially true in a digital age where social media platforms can rapidly amplify false narratives. The public needs to be cautious and rely on credible sources for accurate information, rather than blindly accepting everything they see online.
The recent Signal chat leaks concerning Congress raise intriguing questions about the nature of private communication in the digital age. Understanding the complexities of these leaks requires recognizing the potential for hidden information within encrypted systems. A key concept here is the “black box” approach, where the inner workings of a system, like encrypted messaging apps, are often opaque.
This lack of transparency can be problematic, as illustrated by the recent leaks and their potential implications for political discourse. To better understand this concept, check out this article on the definition of black box. Ultimately, the Signal chat leaks highlight the delicate balance between privacy and accountability in our increasingly digital world.
Role of Social Media in Shaping Public Perception
Social media platforms are uniquely positioned to shape public perception in the wake of such leaks. They allow for rapid dissemination of information, both accurate and inaccurate. This creates a complex environment where public discourse can be influenced by both legitimate news sources and various forms of online manipulation. Social media users need to be critical consumers of information and be aware of potential biases and agendas.
Public Opinion Trends
| Date | Trend | Driving Factors |
|---|---|---|
| Pre-Leak | Generally divided, with some concern about political processes. | Pre-existing political divides, previous scandals, lack of trust in institutions. |
| Immediately Post-Leak | High initial engagement, strong polarization, uncertainty. | Release of information, potential for sensationalism, lack of verified context. |
| Weeks Post-Leak | Continued debate, potential for misinformation and disinformation to spread, emerging narratives. | Debates in news media, social media engagement, emergence of counter-narratives. |
| Months Post-Leak | Diminishing public interest, potential for long-term impacts on political trust. | Shift in public focus, ongoing investigations, eventual resolution or lack thereof. |
Legal and Ethical Considerations
The release of Signal chat leaks concerning Congress raises a complex web of legal and ethical dilemmas. Navigating these issues requires a nuanced understanding of privacy rights, confidentiality, and the responsibilities of journalists and information disseminators. The potential for misuse and the impact on individuals and democratic processes demand careful consideration.The leaks expose a delicate balance between the public’s right to information and the protection of sensitive data.
The ethical implications extend beyond legal boundaries, touching on the principles of responsible journalism and the potential for harm to individuals and institutions.
Legal Implications of the Leaks
The release of private communications, especially those involving public figures, potentially violates privacy laws. Specific legal implications will depend on the content of the leaked material and the jurisdiction involved. Violations of confidentiality agreements or laws related to classified information could also be implicated. Determining the specific legal violations will require careful legal analysis.
Ethical Considerations Surrounding the Release and Dissemination
The ethical considerations are multi-faceted. Disseminating such sensitive information carries significant ethical burdens. Factors to consider include the potential for reputational damage to individuals, the risk of misinformation, and the potential for disruption of democratic processes. The ethical responsibility of the source and recipients of the information is paramount.
Legal Precedents Relevant to the Leaks
Existing legal precedents concerning leaked documents and confidential information offer some guidance. Cases involving whistle-blowers and the release of classified information often serve as a basis for interpreting the legal landscape. The specifics of these precedents are not directly transferable to the current context, but understanding them provides valuable context for analysis. Further investigation into relevant court cases will clarify the application of precedent to the specific circumstances of the leaks.
Responsible Journalism and Reporting
Responsible journalism plays a crucial role in handling sensitive information. The principle of verification and context is critical when reporting on leaked information. Journalists should prioritize accuracy and fairness, and seek to understand the potential consequences of their reporting. Transparency regarding the source of the information and the methods of obtaining it is essential to maintaining public trust.
Thorough vetting and fact-checking of leaked information is essential before publication.
Table of Potential Legal and Ethical Concerns
| Concern | Description | Mitigation Strategies |
|---|---|---|
| Violation of Privacy | Unauthorized disclosure of private communications could violate individuals’ privacy rights. | Strict adherence to ethical guidelines, verification of information, and minimizing the disclosure of personally identifiable information. |
| Violation of Confidentiality | Disclosure of confidential communications could breach confidentiality agreements or other legal obligations. | Careful consideration of the source of the information, verification of its authenticity, and the potential impact on individuals and institutions. |
| Misinformation and Disruption | The release of leaked information could spread misinformation or disrupt democratic processes. | Thorough fact-checking, contextualization of information, and clear identification of sources. |
| Reputational Damage | Leaked information could damage the reputation of individuals or institutions. | Careful consideration of the potential consequences, responsible reporting practices, and the potential impact on individuals and institutions. |
| Security Risks | Leakage could expose vulnerabilities and compromise security. | Minimizing the dissemination of information, protecting sensitive data, and maintaining strict confidentiality protocols. |
Illustrative Scenarios and Examples

The potential consequences of leaked Signal chat transcripts from Congress are far-reaching and complex. These leaks, if verified and disseminated, could expose sensitive information, potentially impacting individuals, institutions, and the public’s trust in the legislative process. Examining historical precedents and potential scenarios provides crucial insight into the potential ramifications.
Hypothetical Scenarios
Leaks of private conversations from congressional proceedings could have devastating consequences. Imagine a leaked exchange revealing a member of Congress lobbying for a specific bill in return for personal gain. This could lead to accusations of corruption, damage the legislator’s reputation, and trigger investigations. Alternatively, sensitive strategic discussions related to international relations or national security, if leaked, could jeopardize diplomatic efforts, compromise national interests, or expose vulnerabilities to adversaries.
Real-World Examples of Similar Leaks
The impact of leaks extends beyond the political sphere. The WikiLeaks disclosures, for example, exposed sensitive diplomatic cables, impacting international relations and trust in governments. The Cambridge Analytica scandal highlighted the potential for misuse of personal data, demonstrating the devastating consequences of data breaches on individuals and societal trust. These cases underscore the importance of careful handling of confidential information and the profound consequences of its unauthorized disclosure.
Impacts on Individuals, Institutions, and Public Trust
Leaks can significantly impact individuals, potentially damaging their careers and personal lives. Institutions, such as government agencies or corporations, may face severe reputational damage, loss of public trust, and legal repercussions. Furthermore, leaks can erode public trust in the institutions and processes responsible for handling sensitive information. The erosion of public trust, in turn, can have profound and long-lasting effects on governance and social cohesion.
Table of Case Studies and Implications
| Case Study | Description | Lessons Learned |
|---|---|---|
| WikiLeaks (2010) | Release of classified diplomatic cables. | Revealed potential for damage to international relations, loss of trust in government transparency, and highlighted the importance of protecting sensitive information. |
| Cambridge Analytica (2018) | Data breach involving personal information of millions of Facebook users. | Demonstrated the significant potential for misuse of personal data and the devastating impact on individuals and societal trust in technology companies. |
| Panama Papers (2016) | Exposure of offshore financial accounts. | Highlighted issues of tax evasion, financial secrecy, and the need for increased transparency in global financial systems. |
| Clinton Email Controversy (2015) | Debate over the handling of classified information by a political figure. | Showed the sensitivity surrounding classified information and the importance of adhering to security protocols. |
Final Conclusion: Signal Chat Leaks Congress
The signal chat leaks congress saga underscores the vulnerability of political communication in the digital age. The potential for misuse and the impact on public trust are significant. This investigation has highlighted the importance of transparency, accountability, and responsible reporting in handling sensitive information. Looking ahead, the repercussions of these leaks will undoubtedly shape future political strategies and communications.
Ultimately, the public’s response will be critical in determining the long-term implications of this event.




